Exodus provides the ability to focus patching and mitigation efforts on which vulnerabilities are relevant, exploitable and affect most networks.
Exodus Intelligence analyzes and documents vulnerabilities that impact business-critical systems. Our expert research covers a diverse set of enterprise software, hardware, common IOT and Industrial Control systems.
We do not just write up the vulnerability details, we provide a proof of concept or exploit for every vulnerability in order to demonstrate the potential impact of the vulnerability and give the customer the ability to test their defenses.
Failed patches leave organizations at risk. Exodus reviews publicly disclosed, exploitable vulnerabilities to verify patch effectiveness and provide corrective guidance to address the root cause of the vulnerability.
Our subscribers can access our library of vulnerability research through The Vault. Each Vulnerability Intelligence Package contains thorough documentation of the vulnerability with packet captures and a proof of concept or exploit.
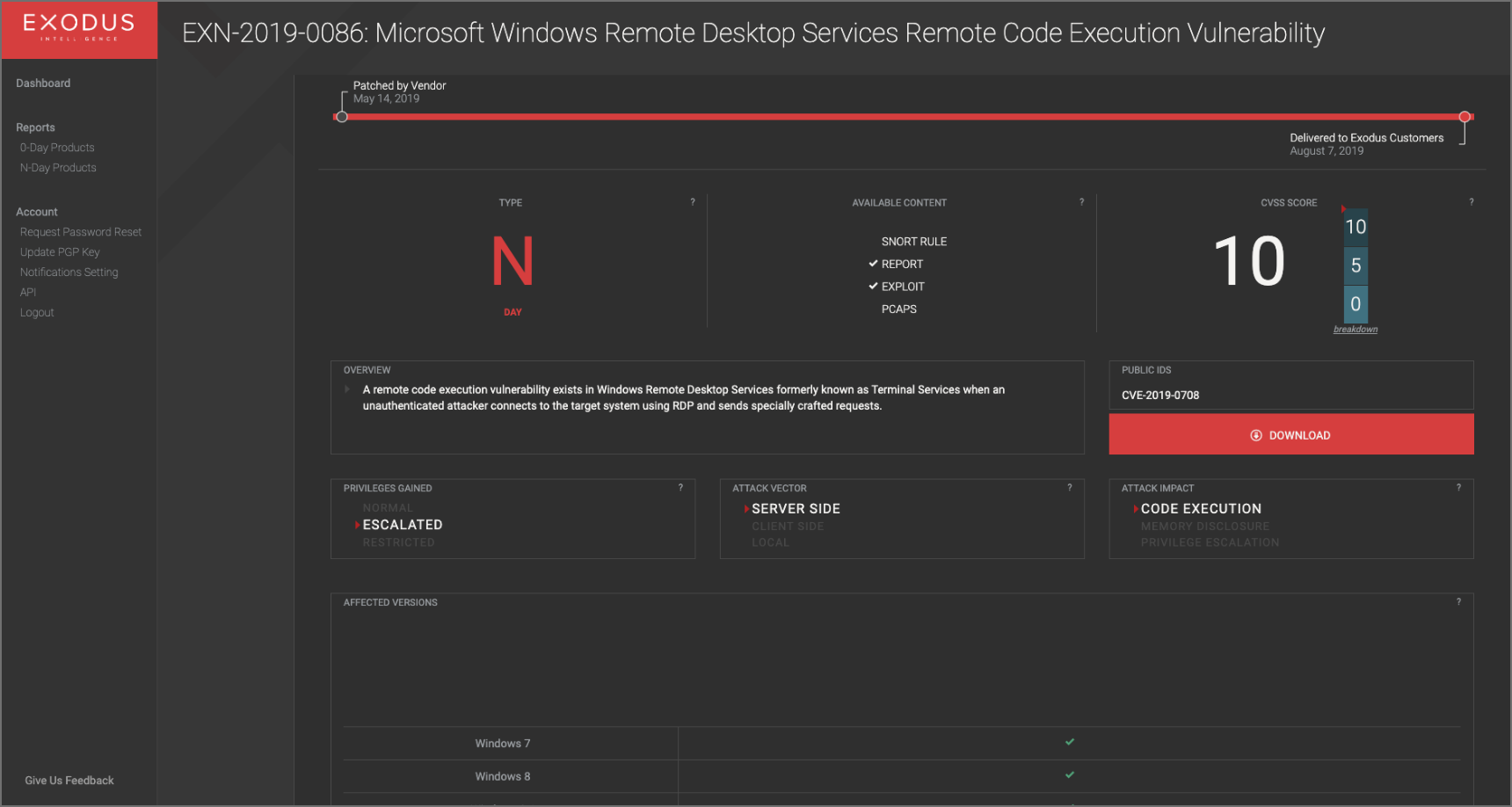
The Vault was designed to prioritize decision-driving information in an easily navigable interface. Users can assess the criticality of the vulnerability at a glance by reviewing:
Exodus offers actionable intelligence that will allow you to test and optimize your defense, with precision. Every vulnerability is well documented and filed securely in the Exodus Vault. Our Vulnerability Intelligence Packages include:
Understand all aspects of the vulnerability
Integrate defenses into third-party detection, prevention and security integration products
Test your defenses with working proof-of-concept or exploit code
See examples of both malicious and benign traffic
The written report is 15 to 30 pages covering all aspects of the vulnerability, including: