Exodus Intelligence
Exodus Intelligence
Detect the undetectable


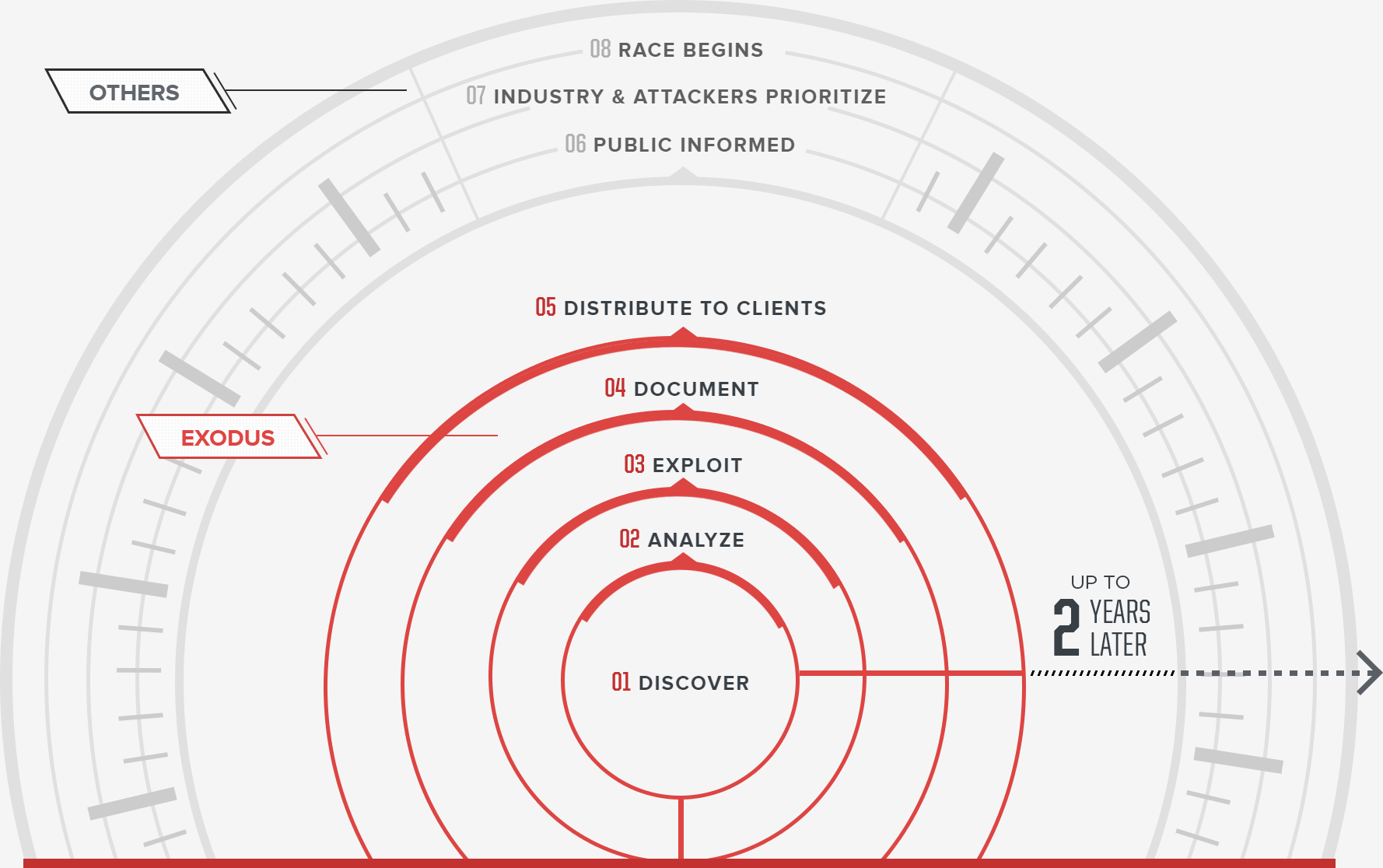
We focus heavily on discovering and exploiting vulnerabilities in business-critical software like enterprise backup solutions, browser, and email clients.
Our exploitation techniques exceed the capabilities of today’s malicious actors which means our customers are prepared for future threats.
Our tools allow users to prove or disprove claims made by defensive products while always being mindful of evasiveness.
Our vulnerability intelligence is securely delivered to our customers via the Vault. We offer multiple subscription levels to fit various security strategies and applications.
Get access to 50 zero-day reports with exploits affecting commercial software and hardware.
Learn more
Expert, thorough analysis and exploitation of high-profile and critical vulnerabilities.
Learn more